I recently bought a USB GPS receiver; it was something I decided I could use with my Raspberry Pi that would be a fun thing to play with for an inexpensive cost and requiring minimal hardware tinkering.

The project I decided to make was a program that scanned for wifi access-points, and recorded their basic information along with the GPS data I was also receiving. I would then roughly map out where wifi hotspots were once I ventured out with my raspberry pi.
The kit
- 1 Raspberry Pi (Model B)
- 1 USB Wifi Receiver (Mine is the GlobalSat BU-353-S4 USB GPS Receiver)
- 1 USB Wifi Adapter (Mine is the ALFA AWUS036H Realtek RTL8187L 1000mW Wireless-G USB WLAN Network Adapter)
- 1 Battery (I got a Anker PowerCore 20100, it provides 20000mAh which should give you close to 24h battery life on the pi)
The code
The full code is available on github: https://github.com/joestrong/hotspotter
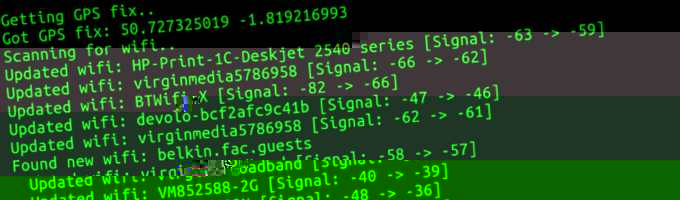
I decided to write the program in nodejs. The reason for this was down to personal preference; I have a lot of javascript experience through web programming.
Through npm I found packages for wifi scanning and reading gps data. I forked the wifi scanner npm package so I could modify it to allow for parsing extra data from the wifi scan.
The results
I was really excited at the results that came back, the GPS accuracy is pretty decent, and the range on the wifi adapter is also really good.
I quickly noticed that I’d inadvertently created a bus detector. A lot of buses came up in the results! When watching the console output in real-time you could see a bus come up before seeing it in person, and you could tell whether you’d seen the bus before by checking the access-point’s mac address.
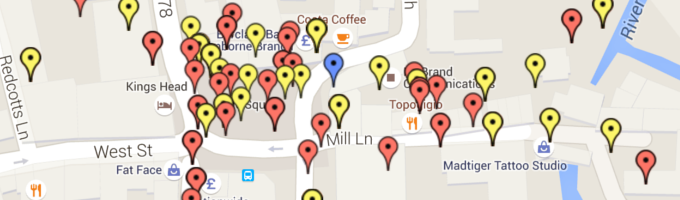
As soon as I created an interactive map that plotted the GPS results, things got even more exciting, and I soon added colour-coding and filtering on the map based on different parameters, such as whether an access-point was public or what security protection they were using.
I was surprised to find that 20% of the wifi access-points were public. In the UK most people’s internet provider tends to be BT, and by default their routers provide public wifi for other BT customers, this is what gives the 20% result.
Thankfully, only around 0.1% of access-points were using the less-secure WEP authentication.
Overall, this was a really fun project to work on, especially as something I had built that interacted with the physical world.